5 min read
JADC2 and the U.S. DoD: Mapping Out the Future of Situational Awareness
 Chip Downing
:
July 26, 2022
Chip Downing
:
July 26, 2022

The unbridled aggression from adversaries in Ukraine has underscored the need to create a military posture that positions the United States and its coalition partners in a constant state of readiness with real-time information and decision-making, and ready to provide real-time situational awareness intelligence to global alliances in their time of need.
This is not a new idea – the U.S. Department of Defense (DoD) created the Joint All-Domain Command and Control (JADC2) strategy that describes the urgent need to empower Joint Force Commanders with the required sensor to command and control (C2) functionality, as well as kinetic and non-kinetic weapon capabilities across all warfighting domains. To deter and, if necessary, defeat any adversary at any time and in any place around the globe.
The JADC2 Strategy requires the unimpeded delivery of real-time situational awareness data to Joint Force Commanders regardless of the military domain or defense supplier. To accomplish this goal, it is vital to embrace the U.S. DoD Data Strategy that transforms the DoD into a data-centric organization that uses data at speed and scale for operational advantage and increased efficiency. In order to “treat data as a weapon system and manage, secure, and use data for operational effect.”1
So how do we enable this real-time delivery of all requisite data and information? Let’s walk through defining what JADC2 is, what some of the challenges of implementing JADC2 are, describe the technology foundations of JADC2, and finally discuss how to implement this new foundation of global real-time intelligence for the Warfighter.
What is JADC2?
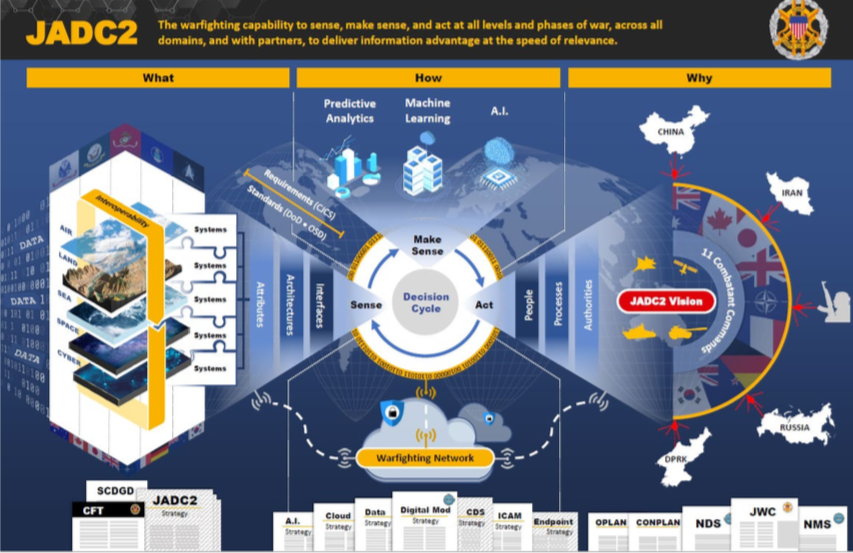
Joint All-Domain Command and Control (JADC2) is the future of global defense systems and an evolution of existing single-supplier, single security domain Command and Control (C2) platforms. It started as a U.S. DoD strategy to enable all branches and allies to "sense," "make sense," and "act" on information across the battlespace quickly by using automation, AI, predictive analytics and machine learning via resilient connectivity. It is evolving simple Sensor-to-Shooter designs to the point where the sensors are now a vast array of radars, commercial and military satellite imagery and other detection devices. These sources feed real-time data into a C2 decision-making entity that determines the appropriate effector that can deliver either a kinetic or non-kinetic response.
Traditionally, weapons systems were delivered by a single supplier as a “self-contained” platform that spanned the sensor-to-C2-to-effector spectrum within a single, dedicated, network-centric operational security domain. JADC2 breaks this architecture apart and, using a data-centric architecture, opens up the sensor-C2-effector information domain to a wide range of suppliers and operators, including coalition partners. It is also designed to select the best effector to launch, instead of a single-supplier weapon system, thus creating operational efficiencies.
JADC2 is also designed to enable a human-in-the-loop to human-on-the-loop to fully autonomous evolution, driving the response time to threats from days/weeks/months to seconds/minutes/hours. Similarly, JADC2 will compress the time in the Observe–Orient–Decide–Act (OODA) loop used for decades in military decision-making.
The official definition of JADC2 is presented in the Summary of the Joint All-Domain Command & Control Strategy, which states: “JADC2 provides a coherent approach for shaping future Joint Force C2 capabilities and is intended to produce the warfighting capability to sense, make sense, and act at all levels and phases of war, across all domains, and with partners, to deliver information advantage at the speed of relevance. As an approach, JADC2 transcends any single capability, platform, or system; it provides an opportunity to accelerate the implementation of needed technological advancement and doctrinal change in the way the Joint Force conducts C2. JADC2 will enable the Joint Force to use increasing volumes of data, employ automation and AI, rely upon a secure and resilient infrastructure, and act inside an adversary's decision cycle.”2
For the purposes of this blog, I am using the term JADC2 as the umbrella term to cover many C2 acronyms, such as C4ISR, C5ISR, Joint All-Domain Operations (JADO), Combined or Coalition JADC2 (CJADC2), Multi-Domain Operations (MDO), and Pan-Domain Capabilities (PDC) and Pan Domain C2 (PDC2).
Click image to view larger.
What is Data-Centricity?
Data centricity refers to a system architecture where data is the primary and permanent asset, and applications come and go. Instead of exchanging statically configured messages, software components communicate via a shared data model where all participants understand the data and data objects appear to applications as local data. Applications directly read and write the value of these objects, which are cached in each participant.
When a data-centric architecture is built upon a peer-to-peer network that does not require servers or brokers as intermediaries, mission-critical real-time data can be delivered to AI and ML engines at wire speed, enabling real-time situational awareness and decision-making.
Enter the U.S. DoD Data Strategy
To enable decision dominance at the speed of war, Joint All-Domain Command and Control (JADC2) systems must provide real-time data to decision makers and decision-making AI and ML systems across different operational commands, from the tactical edge to the fog to the cloud. This aligns precisely with the DoD Data Strategy announced on 30 Sep 2020 which directs U.S. Department of Defense (DoD) leaders to evolve all DoD assets into data-centric assets that treat data as a weapon system. This document outlines seven goals of this strategy -- to make data Visible, Accessible, Understandable, Linked, Trustworthy, Interoperable, and Secure (VAULTIS).
The JADC2 Network Evolution
The U.S. military has well over 10,000 networks it is supporting, and the vast majority of these were built using a network-centric design strategy. Most of these networks were supplied by a single defense contractor and support a single security domain in each network connection. Therefore, sharing data from these networks to entities outside of the original design typically requires a very expensive and hard-to-configure Multiple Independent Level of Security (MILS) or Cross-Domain Switch (CDS), which are also not designed to be rapidly re-configured to provide real-time data to a new point of need.
New data-centric networks reduce the dependency on MILS and CDS platforms and secure individual data elements or topics in shared network pipes with unique authentication, access control, encryption, and data tagging. This eliminates the need for separate network pipes for each security domain and possibly each defense supplier, while allowing for the rapid sharing of real-time data with new coalition partners or agencies.
Top 10 Data Requirements for JADC2
Global militaries are building out the first data-centric networks under the JADC2 umbrella. The U.S. Air Force is building the Advanced Battlefield Management System (ABMS), the U.S. Navy is building Project Overmatch, and the U.S. Army is building both Project Convergence and TITAN. These JADC2 prototype systems are proving that there are now at least ten emerging data-in-motion requirements. The top ten data requirements are:
- Data Centricity
- Network Transport-Agnostic
- Multi-Domain Security Architecture
- Zero Trust / Security
- MOSA / Open Standards
- Cloud-to-Tactical-Edge Connectivity and Enablement
- Design for Disconnected Operations with Data Persistence
- Interoperability
- Scalability
- Network Health Tools
Describing these data requirements is outside the scope of this blog, but further details are available for free as a PDF.
Implementing these Top 10 data requirements into next-generation data-centric networks enables the inclusion of all Armed Services and coalition partners’ combined sensors, command and control, and optimized weapons/effectors systems across our ecosystem. This forms the foundation of a successful, deployable and maintainable JADC2 environment.
RTI Connext: The Leading JADC2 Software Connectivity Framework
RTI Connext®, a TRL-9 commercial product, is already proven in over 1,800 global design wins. Connext is the only technology that satisfies the full spectrum of demanding JADC2 data requirements. Because Connext has an existing deployment footprint in over 75 C2 systems, it vastly reduces the cost, risk, and time of realizing a viable and robust JADC2 environment. Connext peer-to-peer architecture eliminates the need for servers and brokers, enabling real-time access to data for all operational domains. Connext is transport agnostic, working seamlessly across many transports, including TDL, RF, TCP, UDP, Infiniband, Underwater Sensor Network Transports, lossy satellite connections, and even shared memory or backplanes – all in a single compute system.
Connext works reliably even when communication channels are disconnected, denied, intermittent, or have limited bandwidth. Today, Connext is the foundation of over 20 Modular Open Systems Approach (MOSA) standards, and provides the fault tolerance, resiliency and security required by mission-critical JADC2 systems. Connext also works with other network strategies, supports both legacy and future information models, and promotes the deployment of modular systems that can be built and reconfigured dynamically in response to evolving threats. Connext open standard wire protocols and APIs drive seamless integration and interoperability, enabling systems to drive decision dominance at the speed of war.
Conclusion
To support military customers who are working tirelessly to expand and enhance JADC2 compliance, Connext enables a clear, open standards-based migration from network-centric systems to powerful data-centric environments – in many cases using the same network equipment and pipes. This approach is both cost effective and performance-enhancing, making Connext the obvious connectivity foundation for enabling a single unified network that can operate as one. For more information, please visit the JADC2 webpage at rti.com.
References
1Source - U.S. DoD Data Strategy
2Source - Summary of the Joint All-Domain Command & Control Strategy, Department of Defense, March 2022.
About the author
 Chip Downing is Senior Market Development Director, Aerospace & Defense, Real-Time Innovations, Inc.
Chip Downing is Senior Market Development Director, Aerospace & Defense, Real-Time Innovations, Inc.
Chair, FACE Business Working Group Outreach Subcommittee
Posts by Tag
- Developers/Engineer (177)
- Connext DDS Suite (77)
- Technology (74)
- News & Events (73)
- 2020 (54)
- Standards & Consortia (51)
- Aerospace & Defense (48)
- Automotive (35)
- 2023 (34)
- 2022 (29)
- IIoT (27)
- Leadership (24)
- 2024 (22)
- Cybersecurity (20)
- Healthcare (20)
- 2021 (19)
- Connectivity Technology (16)
- Military Avionics (15)
- Culture & Careers (14)
- FACE (13)
- Connext DDS Pro (10)
- JADC2 (10)
- ROS 2 (10)
- 2025 (8)
- Connext DDS Tools (7)
- Connext DDS Micro (6)
- Databus (6)
- Transportation (5)
- Case + Code (4)
- Connext DDS (4)
- Connext DDS Cert (4)
- Energy Systems (4)
- FACE Technical Standard (4)
- Oil & Gas (3)
- RTI Labs (3)
- Research (3)
- Robotics (3)
- #A&D (2)
- Connext Conference (2)
- Edge Computing (2)
- MDO (2)
- MS&T (2)
- TSN (2)
- ABMS (1)
- C4ISR (1)
- ISO 26262 (1)
- L3Harris (1)
- LabView (1)
- MathWorks (1)
- National Instruments (1)
- Simulation (1)
- Tech Talks (1)
- UAM (1)
- Videos (1)
- eVTOL (1)
 Success-Plan Services
Success-Plan Services